Sysdig
Founded Year
2013Stage
Series G | AliveTotal Raised
$728.2MValuation
$0000Last Raised
$350M | 3 yrs agoMosaic Score The Mosaic Score is an algorithm that measures the overall financial health and market potential of private companies.
-16 points in the past 30 days
About Sysdig
Sysdig focuses on protecting cloud environments, containers, and Kubernetes. The company provides services including real-time cloud security, workload protection, vulnerability management, and security posture management. Sysdig serves sectors that require cloud-native application protection and security management. Sysdig was formerly known as Draios. It was founded in 2013 and is based in San Francisco, California.
Loading...
Sysdig's Product Videos
ESPs containing Sysdig
The ESP matrix leverages data and analyst insight to identify and rank leading companies in a given technology landscape.
The cloud detection & response (CDR) market focuses on detecting and responding to security threats in cloud-based systems so that businesses can improve the visibility, threat detection, and incident response capabilities within their cloud infrastructure. These solutions employ advanced techniques like anomaly detection, behavior analytics, and threat intelligence to identify and mitigate cloud-…
Sysdig named as Outperformer among 13 other companies, including Palo Alto Networks, CrowdStrike, and Trend Micro.
Sysdig's Products & Differentiators
Sysdig Platform Architecture
Unified visibility across workloads and cloud infrastructure from a single cloud security and monitoring platform. DevOps teams often implement container and Kubernetes security products and Sysdig is unique by providing unified monitoring and security functionality.
Loading...
Research containing Sysdig
Get data-driven expert analysis from the CB Insights Intelligence Unit.
CB Insights Intelligence Analysts have mentioned Sysdig in 5 CB Insights research briefs, most recently on Jul 28, 2023.

Jul 28, 2023
The cloud security market map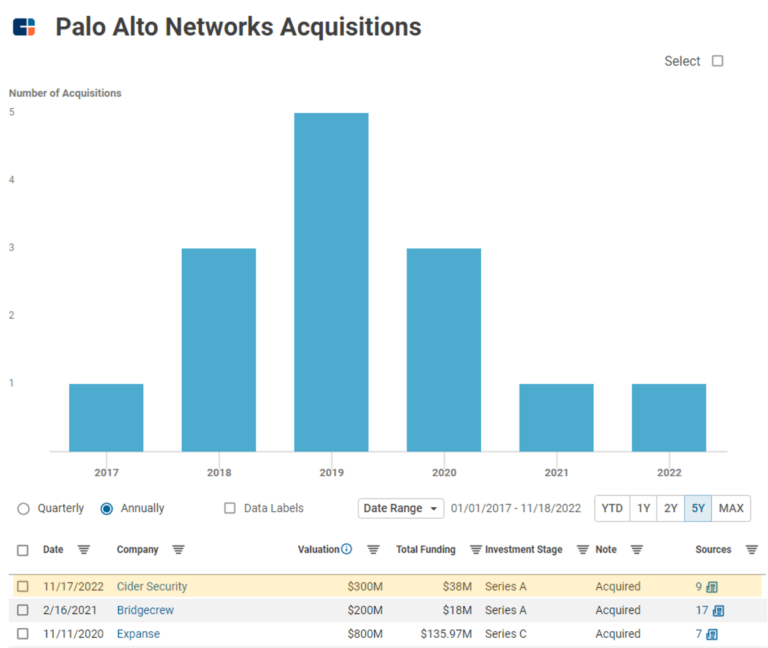

Oct 11, 2022
The Transcript from Yardstiq: Klarna vs. Afterpay
Sep 26, 2022 report
Top cloud security companies — and why customers chose themExpert Collections containing Sysdig
Expert Collections are analyst-curated lists that highlight the companies you need to know in the most important technology spaces.
Sysdig is included in 3 Expert Collections, including Unicorns- Billion Dollar Startups.
Unicorns- Billion Dollar Startups
1,270 items
Tech IPO Pipeline
568 items
Cybersecurity
10,903 items
These companies protect organizations from digital threats.
Sysdig Patents
Sysdig has filed 28 patents.
The 3 most popular patent topics include:
- computer network security
- operating system technology
- computer security
Application Date | Grant Date | Title | Related Topics | Status |
|---|---|---|---|---|
10/28/2022 | 11/5/2024 | Computer security, Web security exploits, Computer network security, Security compliance, Computer security exploits | Grant |
Application Date | 10/28/2022 |
|---|---|
Grant Date | 11/5/2024 |
Title | |
Related Topics | Computer security, Web security exploits, Computer network security, Security compliance, Computer security exploits |
Status | Grant |
Latest Sysdig News
Mar 27, 2025
Cloud Native Now Based in the Holy Land, Tel-Aviv’s Wiz Research team says it has identified a series of unauthenticated Remote Code Execution (RCE) vulnerabilities in the Ingress Nginx Controller for Kubernetes. Dubbed the #IngressNightmare , this vulnerability has the potential to open the door to malicious bad actors. This is the type of vulnerability that can offer unauthorized access to all manner of software system secrets (API keys, passwords, database credentials and so on) stored across all namespaces (logical divisions within a Kubernetes environment) in a Kubernetes cluster. The Role of Ingress Controller Unpacking this nightmare for a moment, let’s remind ourselves that in cloud-native infrastructures, the Ingress concept enables software engineers to map traffic to different backends based on defined rules via the Kubernetes API. An Ingress controller works as a reverse proxy and load balancer to convert configurations from Kubernetes Ingress into routing rules, providing an entry point for external traffic to the services inside the cluster. Although different open-source projects implementing Ingress controllers are available in Kubernetes environments, one of the most popular is Nginx. In terms of how tricky this would be to exploit, there are a few steps to go through, i.e., it’s not as serious as a zero-click interaction on a phone that could allow access to the device, which might then be used for Signal conversations or anything like that. That said, the team does have concerns. According to Wiz researchers Nir Ohfeld, Ronen Shustin, Sagi Tzadik and Hillai Ben-Sasson, “Based on our analysis, about 43% of cloud environments are vulnerable to these vulnerabilities, with our research uncovering over 6,500 clusters, including Fortune 500 companies, that publicly expose vulnerable Kubernetes Ingress controllers’ admission controllers to the public internet – putting them at immediate critical risk. We recommend patching as soon as possible.” The team explains that the job of an Ingress controller is to accept incoming traffic and route it to the relevant Kubernetes services, which in turn forward the traffic to the appropriate pods, based on a set of rules. Ingress Nginx is “explicitly highlighted” in the Kubernetes documentation as an example Ingress controller that fulfills the prerequisite for using Ingress in Kubernetes. Wiz research shows that over 41% of internet-facing clusters are running Ingress-Nginx. “Ingress Nginx deploys an admission controller within its pod, designed to validate incoming Ingress objects before they are deployed. By default, admission controllers are accessible over the network without authentication, making them a highly appealing attack vector,” detail the Wiz team, in a technical advisory blog . “When the Ingress-Nginx admission controller processes an incoming Ingress object, it constructs an Nginx configuration from it and then validates it using the Nginx binary. Our team found a vulnerability in this phase that allows injecting an arbitrary Nginx configuration remotely, by sending a malicious ingress object directly to the admission controller through the network.” Complete Cluster Takeover During the configuration validation phase, the injected Nginx configuration causes the Nginx validator to execute code, allowing remote code execution on the Ingress Nginx controller’s pod. The Wiz team says the admission controller’s elevated privileges and unrestricted network accessibility create a critical escalation path. They note that exploiting this flaw allows an attacker to execute arbitrary code and access all cluster secrets across namespaces. All of which could, ostensibly and practically… lead to complete cluster takeover. Michael Clark, director of threat research at Sysdig, agrees that the Ingress Nginx controller is one of Kubernetes’ most popular Ingress controllers, with thousands of stars on GitHub. “Combining all these vulnerabilities allows an attacker to achieve remote code execution and potentially overall Kubernetes cluster compromise,” explained Clark. “Organizations should prioritize remediating this vulnerability and patch all affected systems immediately. Remediation entails upgrading all instances of Ingress Nginx Controller to the latest version in the environment and ensuring the admission webhook endpoint isn’t publicly exposed.” Among the vulnerabilities reported, Clark and team say that the “most impactful” is the CVE-2025-1974, which allows unauthenticated remote code execution. This class of vulnerability allows an attacker to execute arbitrary code, potentially leading to a cluster-wide impact due to the Kubernetes role assigned to the Nginx Ingress Controller pod. “Since this role has elevated permissions, an attacker could exploit it to escalate privileges within the cluster,” said Clark. “Sysdig also recommends looking for potential examples of activity using Falco for real-time detection – it has not been exploited as far as anyone knows, but the fact that it is so widely used means that it is a potential risk.” Containerization Alone is Not Security The Wiz team caveat all their statements in this space and says that to be clear, gaining initial access to a cluster’s pod network is not as difficult as one might think – containerization on its own is not a strong security boundary. “Many applications running on K8s are susceptible to container escape, as we have repeatedly demonstrated in our research of cloud and SaaS applications over the past few years. Additionally, these vulnerabilities pair very well with SSRF vulnerabilities, which are an arguably common occurrence in web applications,” the Wiz engineers detail. Wiz customers can use the pre-built query and advisory in the Wiz Threat Center. Wiz also validates for exposed admission controllers using the Wiz Dynamic Scanner. Finally, the Wiz Runtime Sensor detects zero-day vulnerabilities like Ingress Nightmare by continuously monitoring ingress traffic, capturing malicious admission review requests in real-time, and flagging anomalous library loads to prevent similar attacks. The Tel-Aviv team thinks that Kubernetes Admission Controllers present an “interesting and often overlooked” attack surface in a Kubernetes environment. They are triggered by the Kubernetes API server to review and potentially modify or block requests before they are processed… and they often run with relatively high privileges within the cluster. “We are only scratching the surface in reviewing the security of admission controllers. Initially, we were surprised to see that such a large code base is used behind the scenes. In our view, this attack surface should be restricted in a much better way: By removing access from pods within the cluster and never exposing this publicly. We were also surprised by the lack of least-privilege design, as the exploit ended up with privileges to take control of the cluster,” notes Wiz. During its research, the Wiz team found other vulnerabilities in Ingres Nginx Controller, and they expect to find more in other admission controllers.
Sysdig Frequently Asked Questions (FAQ)
When was Sysdig founded?
Sysdig was founded in 2013.
Where is Sysdig's headquarters?
Sysdig's headquarters is located at 135 Main Street, San Francisco.
What is Sysdig's latest funding round?
Sysdig's latest funding round is Series G.
How much did Sysdig raise?
Sysdig raised a total of $728.2M.
Who are the investors of Sysdig?
Investors of Sysdig include Accel, Bain Capital Ventures, Insight Partners, Goldman Sachs, Glynn Capital Management and 12 more.
Who are Sysdig's competitors?
Competitors of Sysdig include Solvo, Upwind, Operant AI, Grafana Labs, Aqua Security and 7 more.
What products does Sysdig offer?
Sysdig's products include Sysdig Platform Architecture and 2 more.
Who are Sysdig's customers?
Customers of Sysdig include Beekeeper, WorldPay from FIS and SAP Concur.
Loading...
Compare Sysdig to Competitors

Aqua Security specializes in cloud-native security. The company offers a comprehensive cloud-native application protection platform that provides prevention, detection, and response automation across the entire application lifecycle, securing the build, cloud infrastructure, and running workloads. It primarily serves sectors such as finance and the federal government. Aqua Security was formerly known as Scalock. It was founded in 2015 and is based in Burlington, Massachusetts.

Orca Security focuses on cloud security. It offers a cloud security platform that provides services such as identifying and remediating misconfigurations across clouds, protecting virtual machines, containers, and serverless functions, and monitoring and responding to threats across the cloud attack surface. The company primarily sells to sectors such as financial services, technology, government, retail, healthcare, and media & entertainment. It was founded in 2019 and is based in Portland, Oregon.

Uptycs is a cloud security company that specializes in protecting hybrid cloud environments and providing visibility from development to runtime. The company offers a suite of security solutions, including workload protection, compliance automation, threat detection and response, and security for containers and Kubernetes. Uptycs serves enterprises by optimizing security operations, ensuring compliance, and accelerating remediation across cloud workloads, containers, Kubernetes, and software pipelines from a unified security console. It was founded in 2016 and is based in Waltham, Massachusetts.

Sumo Logic provides cloud-native application security and log management services within the cloud computing industry. Its offerings include a log analytics platform, cloud monitoring, and security information and event management (SIEM) tools. Sumo Logic's solutions are used in sectors such as education, financial services, financial technology, gaming, manufacturing, public sector, and retail. It was founded in 2010 and is based in Redwood City, California.

Deepfence operates within the cybersecurity industry, providing products for the detection, protection, and remediation of threats in cloud and container-native environments. The company's solutions include tools for threat detection, vulnerability management, and compliance monitoring. It was founded in 2018 and is based in Palo Alto, California.

Fairwinds provides Managed Kubernetes-as-a-Service within the cloud-native infrastructure domain. The company offers services including Kubernetes infrastructure management, lifecycle management, and operational efficiency enhancements to assist in the deployment and management of applications on Kubernetes. Fairwinds serves organizations looking to adopt and manage their Kubernetes environments without requiring in-house expertise. Fairwinds was formerly known as ReactiveOps. It was founded in 2015 and is based in Boston, Massachusetts. Fairwinds operates as a subsidiary of Bob Brennan, Robert Ketterson, and William Ledingham.
Loading...